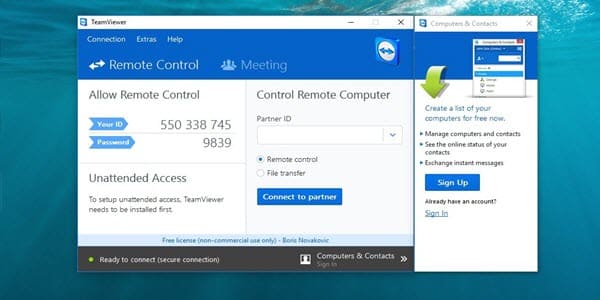
The popular remote login software TeamViewer has stepped up the security game following the recent reports of users’ accounts being hacked. This would not be such important news if it was not for the fact that this tool is installed on millions of computers.
Many people have shared their experience via social media, and the bad news spread like wildfire. Twitter and Reddit were jam-packed with claims of remote attacks carried out by people who have obviously abused TeamViewer accounts. They have lost the cash from bank accounts and are demanding an explanation and calling for justice.
Sitting on the fence
So, let us take a look at this problem from up close. It seems that the attackers have managed to steal a whole bunch of login credentials from popular online shops. Official statements are making people raise their eyebrows, and to make it even worse, the TeamViewer’s spokesman refused to give the exact figures. The company has tried to put the blame on users who employ weak passwords or those that have already been compromised on other websites.
Now, experts from the SecureLink explain that it is completely plausible that those credentials were snatched from giant cashes of data other companies hold:
In mid-May, the contact information of more than 100 million LinkedIn users stolen in 2012 turned up for sale. By late May, Time Inc., confirmed cyber intrusion of MySpace accounts that could have exposed more than 300 million users.
While it is possible that recent breach activity associated with TeamViewer is related to the new availability of black market contact information, TeamViewer users with strengthened security are still reporting hijacked computers.
It could also be that passwords stolen in spectacular breaches were used as a means of bypassing the TeamViewer’s security fence. After all, If Mark Zuckerberg’s account can be accessed without his consent, what can we lesser mortals hope for?
We must acknowledge that many users use the same account information and passwords across the internet. This means that a single strike can make your cyber security fall down like a house of cards. So, the story offered by TeamViewer holds water, but what about the other probable scenario? It does seem too convenient for the company that a large scale theft on social media turns out to be the main driving force behind the attacks. Is the prominent service provider trying to wash their hands?

A dead end
There is a possibility that the remote software’s network did not stand up to the challenge, thus allowing cyber thieves to steal login names and passwords. After all, TeamViewer is now enhancing the security measures, setting up new monitoring capacities for suspicious behavior, and has announced that there will be some “minor inconveniences” as a consequence. Alas, those who have already endured more than that are not buying it.
In the meantime, those who witness their machine being taken over should disconnect and remove all internet access. Unplugging the router, for example, should stop the wrongdoers in their tracks. You can also check the browser history for sites you have not visited, inspect the PayPal accounts, card statements and log files of TV. This incident has also prompted many users to look for alternative services, the solutions for remote support that could prevent such security breaches from occurring.
In case something is amiss, it is advisable to switch to another, clean computer and reset all passwords, this time picking hard-to-guess ones. It is astonishing that feckless passwords such as “12345” still top the lists of most used ones on the internet. Hence, the negligent users definitely share the part of the blame, but pointing fingers is not likely to get us anywhere. We must utilize stronger passwords, and TeamViewer has to establish a more robust security system. That way we can finally form a unified front against evolving cyber threats.
All in the same boat
TeamViewer might have beefed up the security controls, but is it safe to assume that similar attacks will not happen in the future? Well, if that is to happen, another thing must change: The irresponsible use of login credentials. Ultimately, it is of secondary importance whether the users themselves or the company’s network were hacked.
We are in the same boat, and if we let the pirates take the wind out of our sails, we are heading straight for the perilous rocks. This epilogue would be a sorry end to the story, and with all the warning signs, we are under obligation to avoid the collision course.