VPNs have helped us keep our anonymity and privacy intact. They have a major role to play in the dynamic world of internet today. When we hear the word “VPN”, an image of a secure tunnel comes to our mind. However, you may be surprised to know that there are different types of VPN protocols.
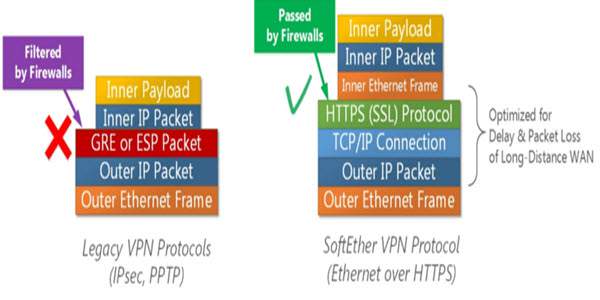 While choosing a VPN service, one needs to have an understanding about different types of VPN protocols that are available. To provide a solution to your problem, we have drafted this comprehensive article to let you understand the various kinds of VPN protocols. This will help you in choosing the best service for you. So, here we go:
While choosing a VPN service, one needs to have an understanding about different types of VPN protocols that are available. To provide a solution to your problem, we have drafted this comprehensive article to let you understand the various kinds of VPN protocols. This will help you in choosing the best service for you. So, here we go:
1. PPTP
This tunneling protocol was developed by a group founded by Microsoft to create VPN over dial-up networks. This protocol uses a variety of authentication methods for providing security.
This VPN protocol is easy to set up and doesn’t require an additional client, which makes it a popular choice amongst business and VPN providers. Its operation is quick owing to the low computational overhead that it requires.
PPTP has lagged behind in competing with its competitors and is now found only with 128-bit encryption keys. A lot of security flaws have cropped up, compelling even Microsoft to issue a notice recommending users to use L2TP or IPSec or SSTP instead. However, the ease of setting up and availability of built-in clients makes it a preferred choice for many, even today.
2. L2TP
This protocol is a unique case. It is one of those VPN protocols that doesn’t provide encryption or confidentiality to the traffic flowing through it. It is usually paired with IPsec encryption to provide privacy and security.
It’s easy to set up and is available across all modern operating systems. A major disadvantage of using this VPN protocol is that it uses UDP port 500 which is almost impossible to be disguised on any other port. This makes it susceptible and difficult to pass around firewalls.
Yes, there are some concerns but the protocol is secure enough. Many a times it fails to pass through firewalls and isn’t very efficient. However, the technically inept users can give it a try considering how easy it is to set up.
3. OpenVPN
OpenVPNs use an open source technology using an OpenSSL library and SSLv3/TLSv1 protocols along with other security measures. This is fairly new, compared to other protocols. The USP lies in the fact that it is easy to configure and use. It is capable of running on any port available though it works best on a UDP Port. This feature makes it almost untraceable by the firewall and hence, is very difficult to block.
Its operation is faster than the two above mentioned protocols. However, the speed is dependent upon the level of encryption it is using.
It is supported by almost all the OS platforms today. Setting up such VPN protocols are slightly difficult as it needs downloading of the client as well as the configuration setups. Overall, the security provided by it is dependable and it is capable of bypassing even the strongest firewalls.
4. SSTP
SSTP (Secure Socket Tunneling Protocol) was first introduced amongst Windows Vista SP1 devices and since then it is available only on Windows platform. Its exclusive availability on Windows platform provides stability and makes it easy of use. It incorporates many advantages of OpenVPN but isn’t open source. It uses AES encryption to provide great anonymity and privacy to its users. An obvious choice for a Windows user.
Conclusion
It’s not very hard to conclude that OpenVPN is the best choice amongst all the available types of VPN protocols. Its flexibility, availability across all software platforms, and ability to bypass even the strongest firewall makes it a preferred choice for the majority of users. However, if you don’t want complexity and want VPN protocols that are easier to set up then you may give others a try. Remember, choices of every individual differs and hence, you should choose according to what best fits your needs.





A nice, handy summary, thanks! Some people (especially mobile users) might be interested to know a bit about IKEv2, which is fast, mobile-friendly, and partially open source using strong encryption. Sadly, it’s also easily detected & thus easily blocked but is still a good choice for online streaming, web browsing and most activities on mobile devices – for more information about IKEv2 see http://www.cogipas.com/vpn-protocols-explained/